OPC-UA certificates
I am trying to write python opc-au client code to communicate to the opc-ua server, however, I cannot figure out the certificates
I have
- set up the opc server to be self-signed by the controller (The following article said this would be the simplest to start with) How to use your own Security Certificate with an OPC UA Server on a PLCnext Control - PLCnext Community (plcnext-community.net))
- Gone to the wbm to download the certificates
- Placed the certificates where my python code is stored
- Ran the python code (used similar to: PLCnext-OPC-UA-connect-minimal/connect.py at master · dschoorisse/PLCnext-OPC-UA-connect-minimal · GitHub)
- I am struggling to see a simple way to actually get past / use the certificates so that the python code could actually use it
Comments
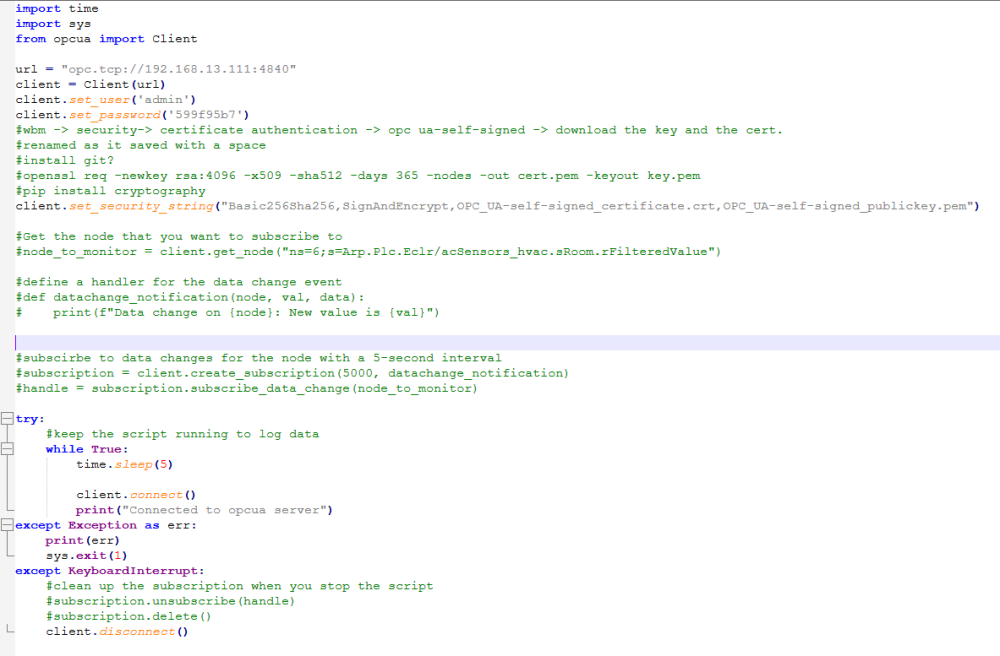
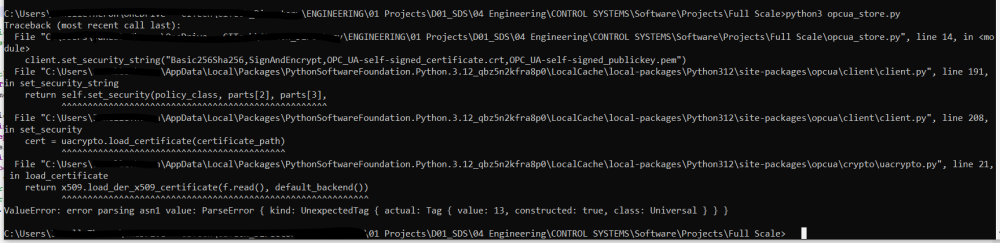
I have also tried to generate my own certificates with the same outcome "ParseError"
I've even tried downloaded a certificate to the plc then re-downloading it so that it had the same name.
I don't know much about python, but I hope some of these suggestions might help:
Ok disabling user authentication worked to confirm that I can connect to the unit
Disabled user authentication, (couldn't find anything in PLCnext to not allow): NB must reboot
The free server connection also worked with no username, password or certificate.
1) Yesterday I did try to use that example's certificates -> tried to upload them to the identity store.
-> They are .der files and the controller wants pem or crt
I tried to load back the security, it rebooted but now the password doesn't work (wbm just reloads each time)
Other things I tried yesterday:
2) Using instructions from this python-opcua/examples/generate_certificate.sh at master · FreeOpcUa/python-opcua · GitHub
made a certificate (both .pem)
openssl req -x509 -newkey rsa:2048 -keyout my_private_key.pem -out my_cert.pem -days 355 -nodes -addext "subjectAltName = URI:urn:example.org:FreeOpcUa:python-opcua"
plcnext -> user file on controller
wbm -> in the identity store saved the certificates
rebooted
Error: Service fault.. uri doesn't match
3) Redownloaded the certificate I just made and saved
Gave the usual asn1 parseerror
4) Tried to generate the certificates in ua config -> when trying to do the certificate part I can only generate a request - did not understand
5) Went back to self-signed by controller, reboot
6) Saved my certificate in the trust store instead
Error was BadCertificateUriInvalid
7) rebooted
Not sure exactly which error but then uaexpert also didn't work.
You shouldn't have to generate or install any custom server certificate on the PLCnext Control device - the default, self-signed server certificate should be enough to start with.
Going back to the third-party OPC UA server - you said:
The free server connection also worked with no username, password or certificate.
How about with security enabled on the third-party OPC UA server? Are you able to successfully establish a connection from your python client in that case? If so, where did you put the server certificate on the client machine, in order to make that work?
Hi Martin, yes I am able to load an example server with a certificate of .der type and a private key of type .pem type and then as a client was able to set the security string with the same certificates, these certificates were placed in the location in which I ran the python code (to both generate the server and the client)
I am still struggling with the original problem though and have made no headway there
In relation to certificates, this should be all that's needed:
If the format of any certificates needs to be changed, you can do this using the openssl command-line tool:
(the OPC UA server certificate downloaded from WBM is a .crt file in PEM format).
The client will also need to provide user credentials during the connection to the server.
I have now gone into this in more detail, and this procedure works:
In PLCnext Engineer:
In Web-based Management:
I used this python example:
I made the following changes to the python script:
client.set_security, I changed the name of the server certificate to the one from the PLC (this is the one in the client's trust store):client.set_security, I added the user credentials for the client:client.set_user('admin') client.set_password('123abc6') # Change this to the admin password on your PLCThis will now establish a connection to the PLC, and you can read and write OPC UA variables in the same way that you did when security was disabled.
Note that the self-signed server certificate may change if you make changes to the OPC UA server settings in PLCnext Engineer, so you might need to copy that to the client again.
Hi Martin, Thanks for the update I will try this soon, unfortunately changing the security on the plc is a bit disruptive as it seems to do a reset of the plc
Dear martin i really needed his help to install plc next , have the error 101
how i can solve this